Hey there, tech enthusiasts! If you're diving into the world of IoT and remote access, you've probably come across the term "remoteIoT platform SSH key." But what exactly is it, and why does it matter? In today's hyper-connected world, securing your devices and networks has never been more important. Let’s break it down for you, step by step, and help you understand everything you need to know about remoteIoT platform SSH keys.
Think of SSH keys as your digital bouncer at a club—they ensure that only authorized users can gain access to your remote systems. With remoteIoT platforms, these keys act as a security mechanism to protect your devices from unauthorized access. Whether you're managing smart home gadgets or industrial IoT systems, SSH keys are your best friend when it comes to securing those connections.
Now, before we dive deeper, let’s set the stage. This article isn’t just another tech jargon-filled piece. We’ll walk you through the basics, the benefits, and the best practices of using SSH keys in remoteIoT platforms. So, whether you're a beginner or an advanced user, stick around—there's something here for everyone!
Read also:Sarah Rose Karr Today The Inspiring Journey Of A Modernday Legend
What is a RemoteIoT Platform?
First things first—what exactly is a remoteIoT platform? Simply put, it’s a system that allows you to manage, monitor, and control IoT devices remotely. These platforms serve as the backbone for IoT ecosystems, enabling seamless communication between devices and users. From agriculture to healthcare, remoteIoT platforms are revolutionizing industries by providing real-time data and control.
But here’s the catch—these platforms are only as secure as the measures you put in place. That’s where SSH keys come into play. By using SSH keys, you can ensure that your remoteIoT platform remains protected from hackers and cyber threats.
Why SSH Keys Matter for RemoteIoT Platforms
SSH keys are essentially cryptographic keys that provide a secure way to authenticate users and devices. Unlike traditional passwords, SSH keys offer a higher level of security and are much harder to crack. Here’s why they matter:
- Enhanced Security: SSH keys use complex algorithms that make them nearly impossible to brute-force.
- Convenience: Once set up, SSH keys eliminate the need for repetitive password entry, saving you time and hassle.
- Scalability: As your IoT network grows, SSH keys make it easier to manage multiple devices without compromising security.
By integrating SSH keys into your remoteIoT platform, you’re not just securing your data—you’re future-proofing your IoT infrastructure.
How Do SSH Keys Work?
Let’s get technical for a moment. SSH keys work on a principle called public-key cryptography. Here’s a quick breakdown:
Public Key: This is the key you share with the server or device you want to connect to. Think of it as your business card—it identifies you to the system.
Read also:Titan Nathaniel Fiennestiffin The Rising Star Redefining Hollywood
Private Key: This is the key you keep secret. It’s like your personal ID card—only you should have access to it. When you try to connect to a server, the private key is used to prove your identity.
When you attempt to log in to a remoteIoT platform, the system checks your public key against your private key. If they match, you’re granted access. Simple, right?
Benefits of Using SSH Keys for RemoteIoT Platforms
Now that you understand the mechanics, let’s talk about the benefits. Here’s why SSH keys are a game-changer for remoteIoT platforms:
1. Superior Security
SSH keys are far more secure than passwords. They use advanced encryption algorithms that make them nearly impossible to crack. Plus, they eliminate the risk of password-based attacks like phishing and brute-force attempts.
2. Easy Scalability
As your IoT network expands, managing multiple devices can become a challenge. SSH keys simplify this process by allowing you to manage access for multiple devices with ease.
3. Automation Potential
SSH keys can be used in automated scripts and processes, making them ideal for large-scale IoT deployments. This reduces the need for manual intervention and minimizes the risk of human error.
4. Cost-Effective
Implementing SSH keys doesn’t require additional hardware or software. It’s a cost-effective solution that delivers significant security benefits.
With these advantages, it’s no wonder that SSH keys have become the go-to solution for securing remoteIoT platforms.
Setting Up SSH Keys for Your RemoteIoT Platform
Ready to get started? Setting up SSH keys for your remoteIoT platform is easier than you think. Follow these steps:
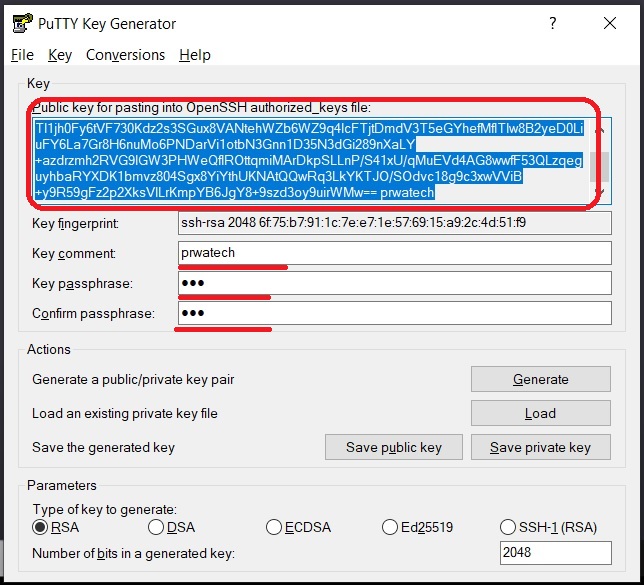
- Generate Keys: Use a tool like ssh-keygen to generate your public and private keys. Make sure to save them in a secure location.
- Install Public Key: Copy your public key to the server or device you want to connect to. Most remoteIoT platforms have a straightforward process for this.
- Test Connection: Try connecting to the server using your private key. If everything is set up correctly, you should gain access without entering a password.
Pro tip: Always use strong, unique keys and store your private key securely. Avoid sharing your private key with anyone—it’s like giving them the keys to your kingdom!
Best Practices for Managing SSH Keys
Now that you’ve set up your SSH keys, here are some best practices to keep them secure:
- Limit Access: Only grant SSH key access to trusted users and devices.
- Regularly Update Keys: Periodically rotate your SSH keys to minimize the risk of unauthorized access.
- Use Strong Encryption: Opt for modern encryption algorithms like RSA 4096 or ED25519 for maximum security.
- Monitor Activity: Keep an eye on login attempts and unusual activity to catch potential security breaches early.
By following these practices, you can ensure that your SSH keys remain a robust security measure for your remoteIoT platform.
Common Challenges with SSH Keys in RemoteIoT Platforms
While SSH keys are incredibly powerful, they’re not without their challenges. Here are some common issues you might face:
1. Key Management
As your IoT network grows, managing multiple SSH keys can become cumbersome. Use tools like SSH certificate authorities or key management systems to streamline the process.
2. Key Rotation
Regularly rotating SSH keys is essential for security, but it can be time-consuming. Automate this process wherever possible to save time and reduce errors.
3. Compatibility Issues
Not all remoteIoT platforms support SSH keys out of the box. Make sure to check compatibility before implementing them in your system.
By addressing these challenges proactively, you can maximize the benefits of SSH keys while minimizing potential issues.
Real-World Applications of SSH Keys in RemoteIoT Platforms
Let’s look at some real-world examples of how SSH keys are being used in remoteIoT platforms:
1. Smart Agriculture
Farmers are using remoteIoT platforms to monitor soil moisture, weather conditions, and crop health. SSH keys ensure that only authorized personnel can access this sensitive data.
2. Healthcare IoT
Hospitals and clinics rely on IoT devices for patient monitoring and diagnostics. SSH keys protect these devices from cyberattacks, ensuring patient data remains secure.
3. Industrial Automation
Manufacturing plants use IoT sensors to optimize production processes. SSH keys play a crucial role in securing these systems, preventing downtime and data breaches.
These examples highlight the versatility and importance of SSH keys in various industries.
Future Trends in RemoteIoT Platform Security
As technology evolves, so do the methods for securing remoteIoT platforms. Here are some trends to watch out for:
1. Quantum-Resistant Encryption
With the rise of quantum computing, traditional encryption methods may become obsolete. Researchers are developing quantum-resistant algorithms to future-proof SSH keys.
2. AI-Powered Security
Artificial intelligence is being used to detect and respond to security threats in real-time. This technology can enhance the effectiveness of SSH keys by identifying potential breaches before they occur.
3. Blockchain Integration
Blockchain technology offers a decentralized approach to key management, making it harder for hackers to compromise SSH keys. This could revolutionize how we secure remoteIoT platforms in the future.
Staying ahead of these trends will help you maintain a robust security posture for your remoteIoT platform.
Conclusion
So there you have it—a comprehensive guide to remoteIoT platform SSH keys. From understanding the basics to implementing best practices, we’ve covered everything you need to know to secure your IoT ecosystem.
Remember, security isn’t a one-time task—it’s an ongoing process. By regularly updating your SSH keys, monitoring activity, and staying informed about the latest trends, you can ensure that your remoteIoT platform remains safe and secure.
Now it’s your turn! Have you implemented SSH keys in your remoteIoT platform? Share your experiences in the comments below. And don’t forget to check out our other articles for more insights into the world of IoT and cybersecurity.
Table of Contents
- What is a RemoteIoT Platform?
- Why SSH Keys Matter for RemoteIoT Platforms
- How Do SSH Keys Work?
- Benefits of Using SSH Keys for RemoteIoT Platforms
- Setting Up SSH Keys for Your RemoteIoT Platform
- Best Practices for Managing SSH Keys
- Common Challenges with SSH Keys in RemoteIoT Platforms
- Real-World Applications of SSH Keys in RemoteIoT Platforms
- Future Trends in RemoteIoT Platform Security
- Conclusion